Previse Writeup - HackTheBox
Previse box from HackTheBox it's a fun, interesting box and close to the real world. For some reason I really liked this box!
Welcome to the writeup of Previse box from HackTheBox. It was a fun, interesting box and close to the real world, working on curiosity to solve and get inside. | |||||||||||||||||
Without further ado, let's get down to business! | |||||||||||||||||
| |||||||||||||||||
NMAP | |||||||||||||||||
| |||||||||||||||||
Added 10.10.11.104 -> previse.htb to /etc/hosts. | |||||||||||||||||
| |||||||||||||||||
Performed a brute-force with the Gobuster tool. | |||||||||||||||||
GOBUSTER | |||||||||||||||||
| |||||||||||||||||
I could find others pages in /nav.php source code that were not initially listed with Gobuster. | |||||||||||||||||
| |||||||||||||||||
| |||||||||||||||||
Even with knowledge of existing pages we need to be authenticated to access them. | |||||||||||||||||
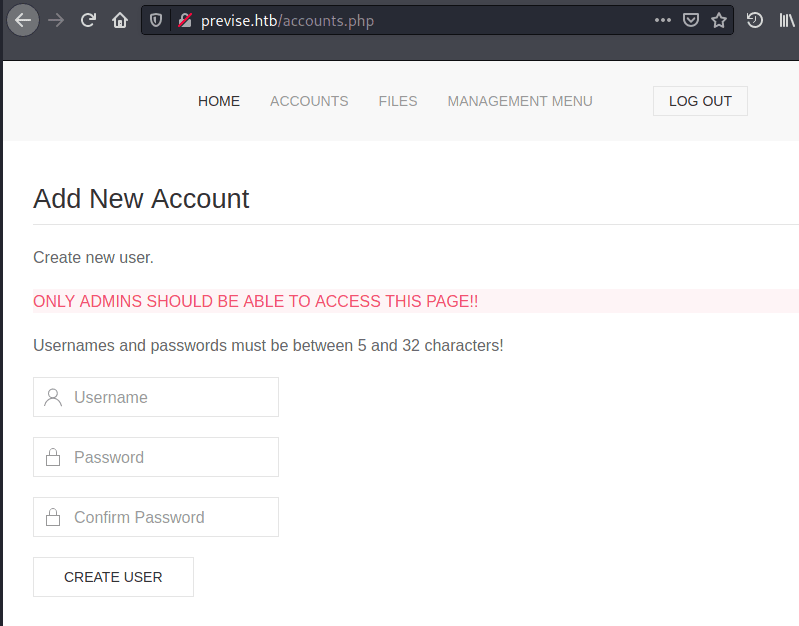
Used Burp to intercept and tamper the response to change status code from 301 to 200 "OK" and send the response. Doing that I could bypass to access the pages and create an account. | |||||||||||||||||
| |||||||||||||||||
According to the permissions and informations on the page the new account ("NAP00") is apparently an "administrator" account. | |||||||||||||||||
| |||||||||||||||||
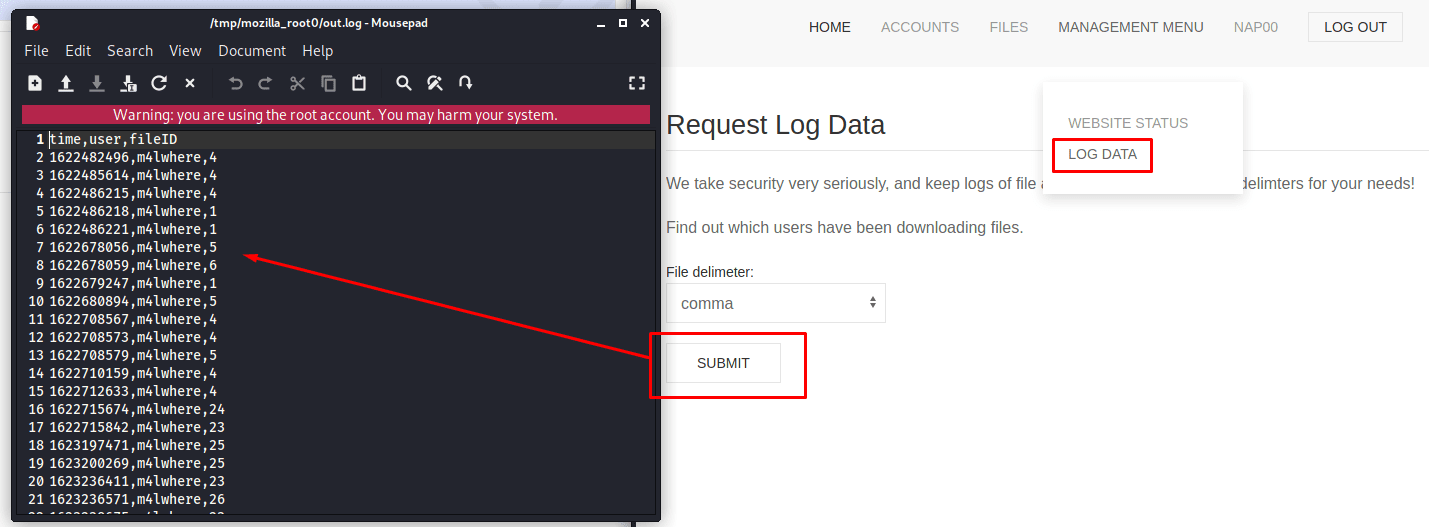
With this access I was able to internally map the site and access previously identified pages that were not initially allowed, which made it possible to identify potential users. | |||||||||||||||||
| |||||||||||||||||
User identified at log data: m4lwhere. | |||||||||||||||||
At Files > Uploaded files was possible to download siteBackup.zip and get the source code of the pages listed before. | |||||||||||||||||
| |||||||||||||||||
In config.php page has the user and pass from MySQL service connection. | |||||||||||||||||
| |||||||||||||||||
But this information did not allow me a shell now :( | |||||||||||||||||
Returning to the page source code reviews searching for possible flaws was found the exec() function and it was possible to abuse it for code execution. | |||||||||||||||||
| |||||||||||||||||
Used Burp to intercept the request from logs.php page and test the code execution. | |||||||||||||||||
| |||||||||||||||||
Well, that worked! | |||||||||||||||||
Replayed the request calling the binary /bin/bash to get a reverse shell on port 6666. Awaited connection with netcat. | |||||||||||||||||
| |||||||||||||||||
| |||||||||||||||||
| |||||||||||||||||
Finally, We are inside! But our permissions are limited... | |||||||||||||||||
As identified before, the application makes a connection to the database using the MySQL credentials found on the config.php, using this credentials was possible to access the database successfully and m4lwhere's password hash was found. | |||||||||||||||||
| |||||||||||||||||
Used hashcat to decrypt the hash with rockyou.txt wordlist. | |||||||||||||||||
| |||||||||||||||||
| |||||||||||||||||
Used ssh to connect as m4lwhere user. | |||||||||||||||||
| |||||||||||||||||
Logged as m4lwhere was possible to get the user flag. | |||||||||||||||||
| |||||||||||||||||
Privilege Escalation | |||||||||||||||||
Now we need to escalate our privilege and to do that we can use the command: sudo -l. Which informs sudo permission for /opt/scripts/access_backup.sh script. | |||||||||||||||||
| |||||||||||||||||
Analyzing the /opt/scripts/access_backup.sh script, you can see that some commands/binaries are called directly and there may be the vulnerability of "path injection". | |||||||||||||||||
In a directory with permissions (/dev/shm) I configured the environment variable $PATH for my current directory and created the "date" file containing a netcat command to return a reverse shell on port 6699. | |||||||||||||||||
After that, executing the script with sudo it will run my "new" date file as root and hence the netcat command. | |||||||||||||||||
| |||||||||||||||||
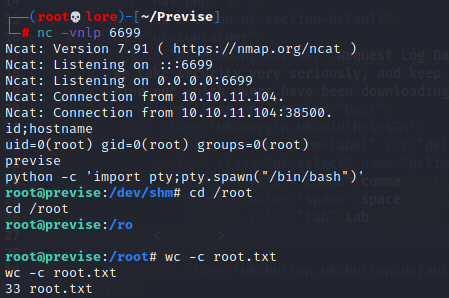
Received the reverse shell connection as root successfully! | |||||||||||||||||
Improved reverse shell with python and get root flag o/ | |||||||||||||||||
| |||||||||||||||||
Conclusion | |||||||||||||||||
Despite being classified as easy, it wasn't that "easy". The second flag (root flag) its not complex - and yet it stayed close to the real world, because many are concerned about external security, but don't "believe" in internal access (don't be like that!) - but to get the first flag (user flag), as you could see, it was a FUN job XD | |||||||||||||||||
For some reason I really liked this box! And I send my special thanks to "m4lwhere" - the creator of this box. | |||||||||||||||||
| |||||||||||||||||
Thanks for reading and feel free to pingback a coffee ;D | |||||||||||||||||
naP0 | |||||||||||||||||
| Deixe seu Pingback |